What Are Industrial Thin Clients? Part 1/2—How It Works
Content of This Article
What Are Industrial Thin Clients? Part 1/2—How It Works
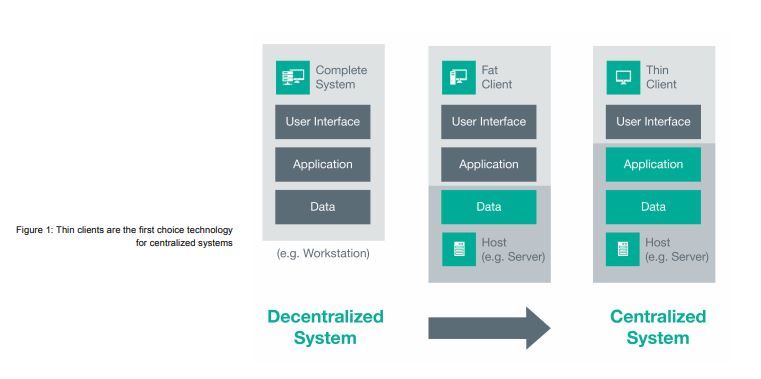
Explosive atmospheres, harsh environments, extreme temperatures – the process industry places special demands on people and technology. This also applies to so-called thin clients, as they are known from office applications. Unlike classic PCs, thin clients do not run applications locally, but on remote servers, and only the image information and inputs are transmitted over the network.
Over the last decade, thin clients have become increasingly popular in process automation and industrial applications. In particular, the trend towards virtualization makes thin clients a cost-effective solution. This allows users to access applications and information running on centralized systems – for example – servers.
Compared to conventional, decentralized automation systems, on which all data and applications usually run, those of centralized automation systems are usually stored on servers. Here, a thin client provides the user interface to make relevant applications and information accessible from the host.
To achieve this, a thin client has a minimalist, usually embedded operating system (OS) and provides drivers for input and output devices (e.g.: mouse, keyboard, touch screen and monitor) that are connected to the thin client. Established communication protocols allow the exchange of system inputs and outputs between the thin client and the server.
How Do Remote Protocols Work?
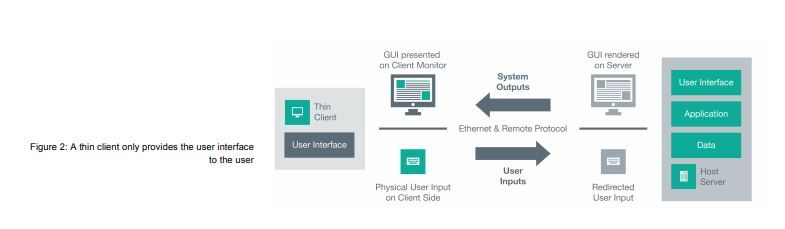
The server generates a user interface (graphical user interface or GUI for short), which it compresses and transfers to the thin client as a remote protocol via an Ethernet connection. The thin client receives the compressed data, for example in the form of GUI images, extracts it, and displays it on the user’s screen.
Input from the user, for example via the keyboard, mouse, or touch screen, is sent in the opposite direction. The thin client receives the user’s physical inputs and forwards them to the server via the remote protocol. The server decrypts the inputs and transfers them to the underlying operating system and the respective applications. The applications implement the commands in the same way as they do for local inputs on operating systems. The high-performance Ethernet that is available today means that users experience the interactions on the thin client as if they were working with the operating system itself.
Since thin clients communicate over Ethernet, thin client technology has become one of the most popular options for virtualized automation systems. Conventional technologies such as keyboard, video, and mouse extenders (KVM) are not compatible with virtualized systems. This is because there are usually one or more virtual machines (VMs) running on the servers, and therefore the physical interfaces are not sufficient for networking with KVMs. VMs can only be accessed over the network using remote protocols.
What Remote Protocols Are Available?
Numerous protocols are now available. The following remote protocols are most relevant for virtualization:
- Microsoft® Remote Desktop Protocol (RDP): RDP is the most popular remote protocol for workplace-based and virtualized automation systems. While Microsoft’s latest operating system can be accessed via an integrated RDP user interface, for example for remote management, professional installations require a Windows OS server. Due to Microsoft’s infrastructure virtualization strategy, and since the launch of Windows Server 2008 R2 in 2009, terminal services have been expanded, and have been renamed Remote Desktop Services (RDS).
- Virtual Network Computing (VNC): VNC is one of the oldest remote protocols that is still well-known today. These protocols have been used mostly in smaller, non-virtualized automation systems ever since several “open source” implementations have been in place. These allow cost-effective solutions to be created.
- Citrix® Independent Computing Architecture (ICA): ICA is a Citrix-protected, platform-independent remote protocol used in large, professional, and virtualized infrastructures with Citrix XenApp and XenDesktop.
- VMware PC-over-IP (PCoIP): Originally established by Terradici®, VMware has integrated this protocol into its virtualized server structure. In addition to PCoIP, VMware supports access to the hosted VMs via RDP
More Information
Subscribe to our newsletter and receive regular news and interesting facts from the world of automation.